Firewall Evasion
Fragmentation
It will divide the tcp Packet into small chunks so that if any firewall encounters these fragments, it will simply either look for the first fragment which may not contain the full TCP header or also say that the fragments may follow different paths which again makes it difficult for the firewall to reassemble these fragments.
nmap -f 192.168.1.6
Decoys
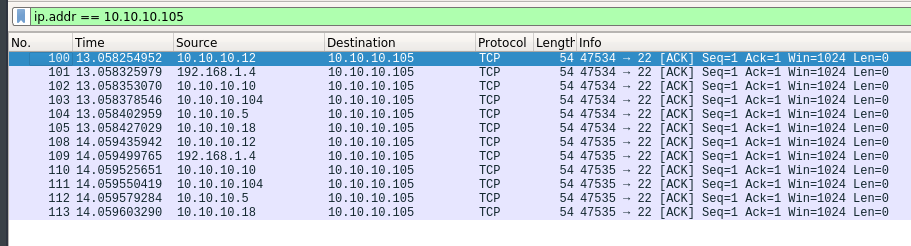
In this we simply instruct nmap to spoof packets from other hosts. When such scan is used, then the logs generated in target firewall has many others IP other than the attacker IP.It becomes harder to determine from which system scan is being done.
There are two ways to use it:
nmap -D RND:5[target IP]
ornmap target -D decoy1,decoy2,decoy3,decoy4 -S source_IP -p 22-25
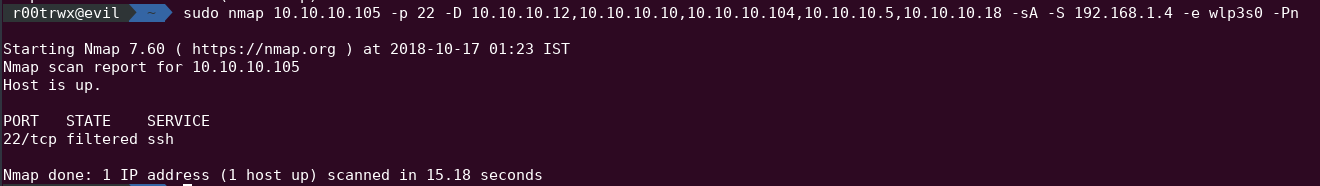
orsudo nmap 10.10.10.105 -p 22 -D 10.10.10.12,10.10.10.10,10.10.10.104,10.10.10.5,10.10.10.18 -sA -S 192.168.1.4 -e wlp3s0 -Pn
IDLE Scan
In this, we look for an IDLE system inside a network, which can talk to our target system.We first send a packet SYN/ACK and wait for response, we note down the ID value(say 45). Next we spoof ourself to be the IDLE system and send a SYN packet to Target. Target then sends the SYN/ACK to IDLE system and in return IDLE system replies back with ID value which is incremented by 1(say 46). Next we again send a SYN/ACK packet to IDLE system and wait for its reponse, It will send ID value incremented by 1 again(say 47).Hence we can see that the Our IDLE system is talking to target system and hence port is open. It maintains our anonymity.
nmap -sI 192.168.1.4 192.168.1.7
where 192.168.1.4 is IDLE system and 192.168.1.7 is target system
Avoiding IDS Detection
- Using low Template no i.e, T