Nmap Scripting Engine(NSE)
It is one of Nmap's most powerfull feature. It automates a wide variety of tasks. NSE can be helpfull in following areas:
- Network Discovery
- http-headers
- http-email-harvest
- http-chrono
- nbstat
- ipidseq
- Vulnerability Detection
- ssl-heartbleed
- http-csrf
- smtp-vuln-cve2011-1720
- Version Detection
- pptp-version
- stun-version
- skypev2-version
- Backdoor Detection
- ftp-proftpd-backdoor
- irc-unrealirced-backdoor
- Vulnerability Exploitation
- jdwp-exec
- http-stored-xss
Nmap has divided NSE into different script categories like :
- Auth
- Broadcase
- brute
- Default category
- Discovery
- Dos
- Exploit
- External
- fuzzer
- intrusive
- malware
- safe
- version
- vuln
Calling NSE
There are two ways to call NSE:
nmap -sC 10.10.10.91
This -sC looks for all the default category of Nmap scripts present in Nmap. It may take a lot time scanning time as it is going to use multiple scripts.
nmap --script dns-service-discovery google.com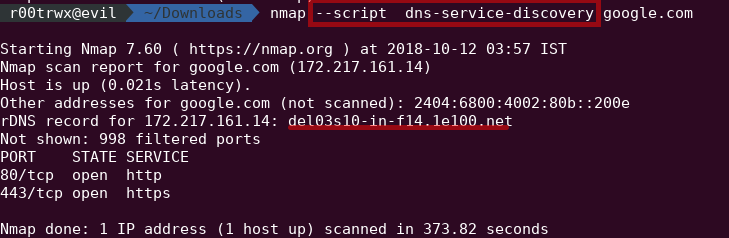
Using this way we can refine our scan to one or two scripts again saving our time of scan.
As in this, we can see it simply went for reverse DNS discovery of google.com
Example:
- Looking for http-header, http-chrono
nmap --script http-headers,http-chrono 192.168.0.104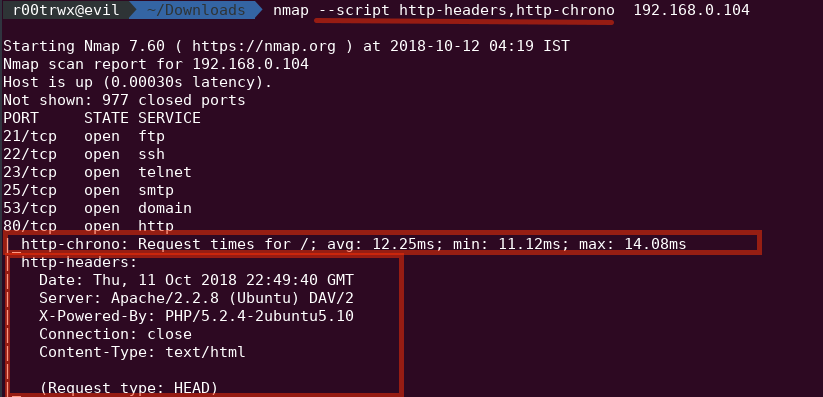
Scanning and Auditing Web Servers
Checking for Misconfiguration
- Listing HTTP Methods
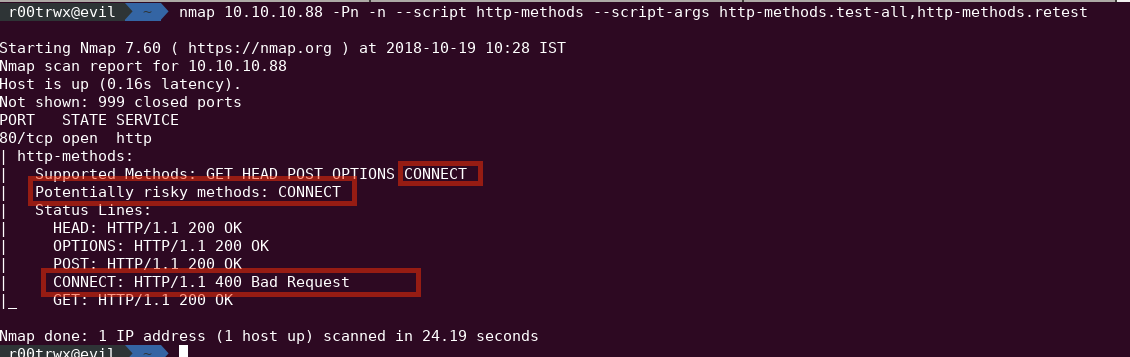
Using http-methods we can discover type of HTTP methods allowed. Based on the methods we can process further.nmap 10.10.10.88 --script http-methods -Pn -n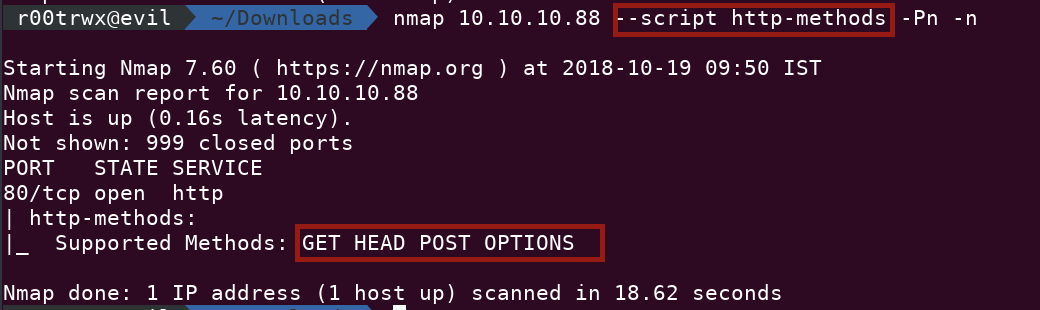
Lets dig a little deeper using script-args by nmap nse
nmap 10.10.10.88 -Pn -n --script http-methods --script-args http-methods.test-all,http-methods.retest
- Directory Enumeration
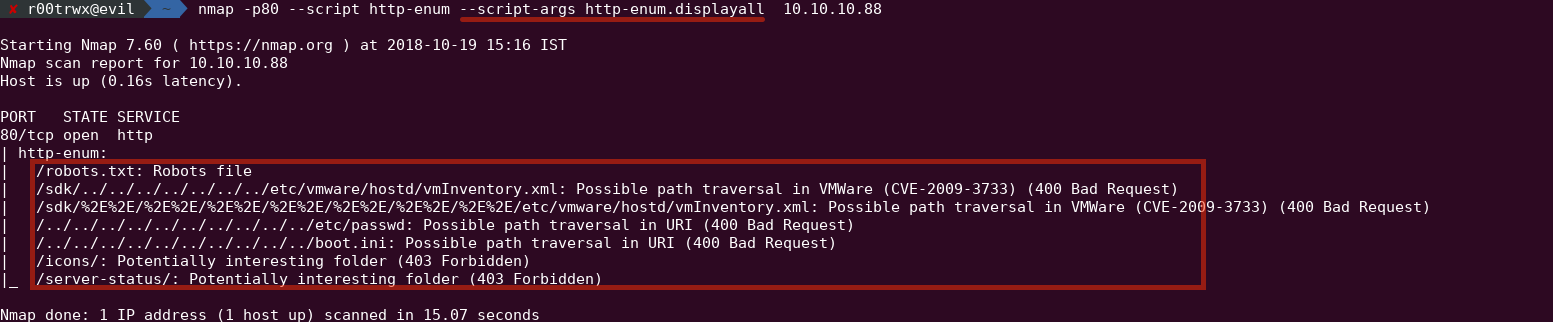
nmap -p80 --script http-enum 10.10.10.88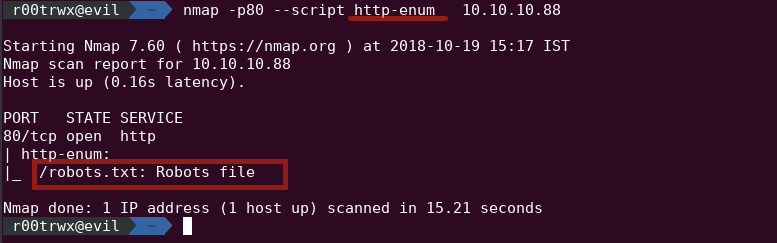
Now if you want to dig a little deeper then use http-enum.displayall
nmap -p80 --script http-enum --script-args http-enum.displayall 10.10.10.88