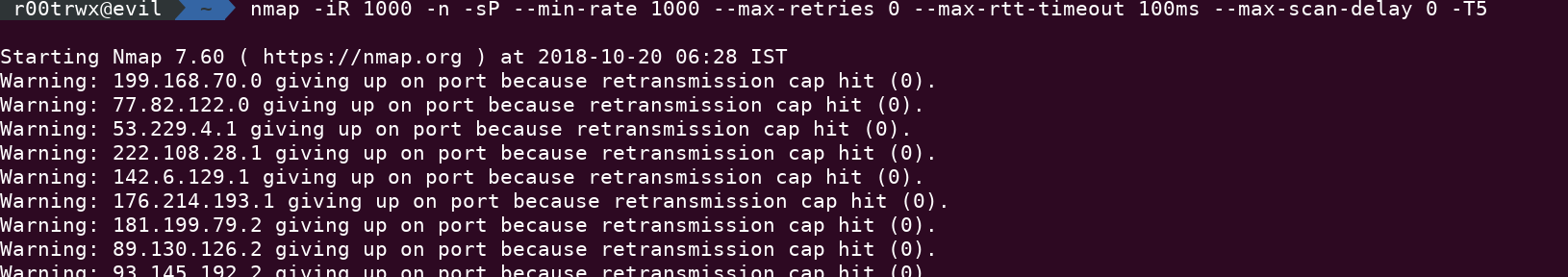
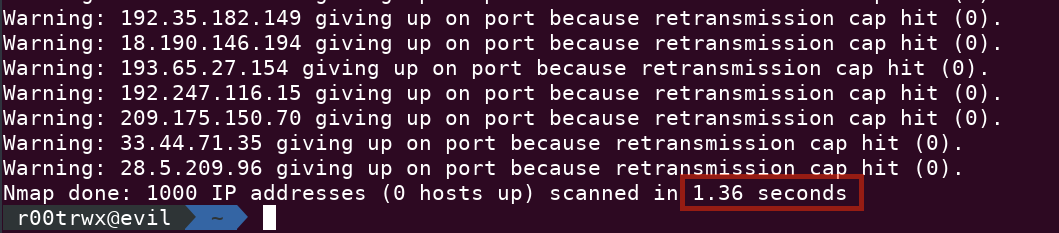
Performance and Timings
Time management is one of important factor of Nmap because we are always limited too time. It is okay when we have to scan single target host/IP but what if there are hundreds of target host. Also scans like Version detection, UDP scanning, OS detection take more time to scan. Now the good part is that Nmap provides various time management option via which we can optimise our scans with accuracy Some of the best practices to get maximum performance are ;
- --host-timeout:
sudo nmap -Pn -p 80,443,22 -sV -O --host-timeout 10s google.com
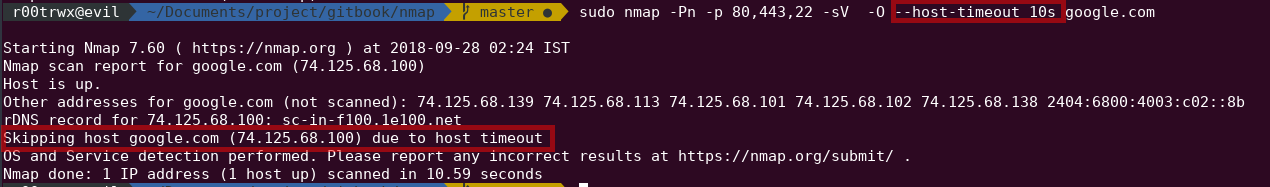
--host-timeout is used for maximum time before giving up on a whole host. In above example I have given 10s after which it will give up on google.com. In scan result we can see it was able to perform half scan and as 10s passed it gave up on google.com. Using such method you can specify timeout, so that if a target host is taking enough time it can skip it.
- --max-retires : Sometimes, due to poor network reliability or no response to a port scan probe/request(port may be filtered) may require retransmission of the port scan request. Now if retransmission occurs again and again then it will increase time complexity. Thats why we use --max-retires to specify how many retransmission should occur on failure of port scan probe.
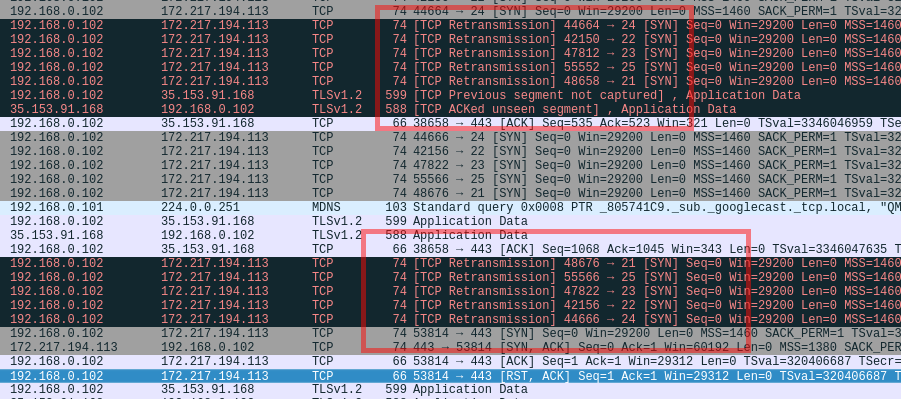
Example of normal scan when ports filtered
nmap -p 21-25 google.com
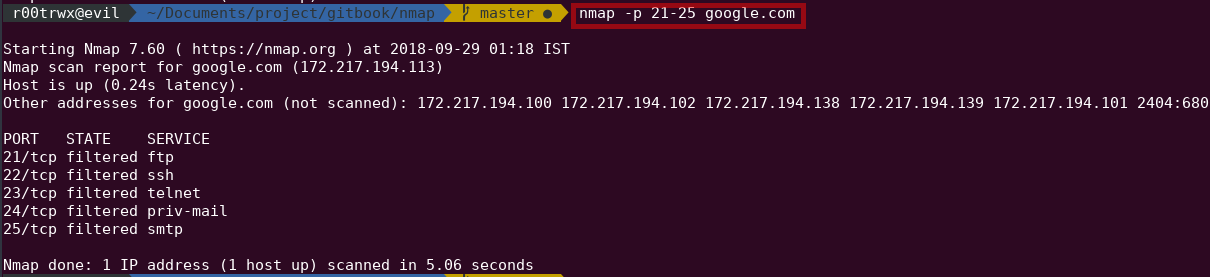
After doing this scan when I captured my traffic in wireshark, I saw that there were 2 retransmission.
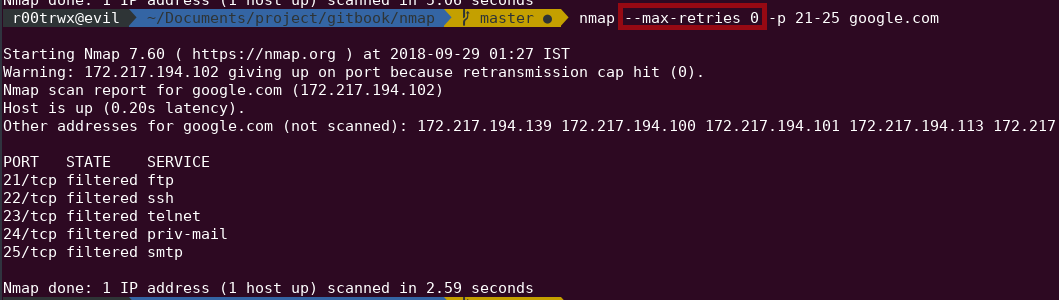
Now after using --max-retriesnmap --max-retries -p 21-25 google.com
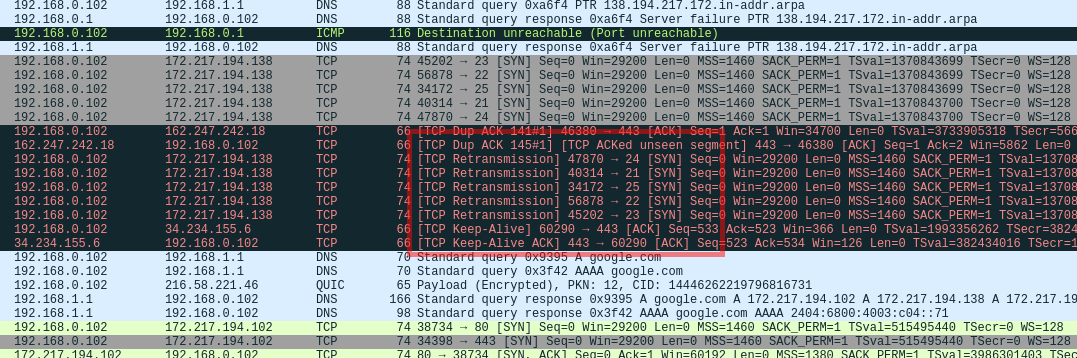
Now when captured traffic in wireshark
--max-rate : This specifies at what rate packets are to be send at a time.
--min-rate: Specifies minimum no. of packet per second.
- Example
nmap -iR 1000 -n -sP --min-rate 1000 --max-retries 0 --max-rtt-timeout 100ms --max-scan-delay 0 -T5