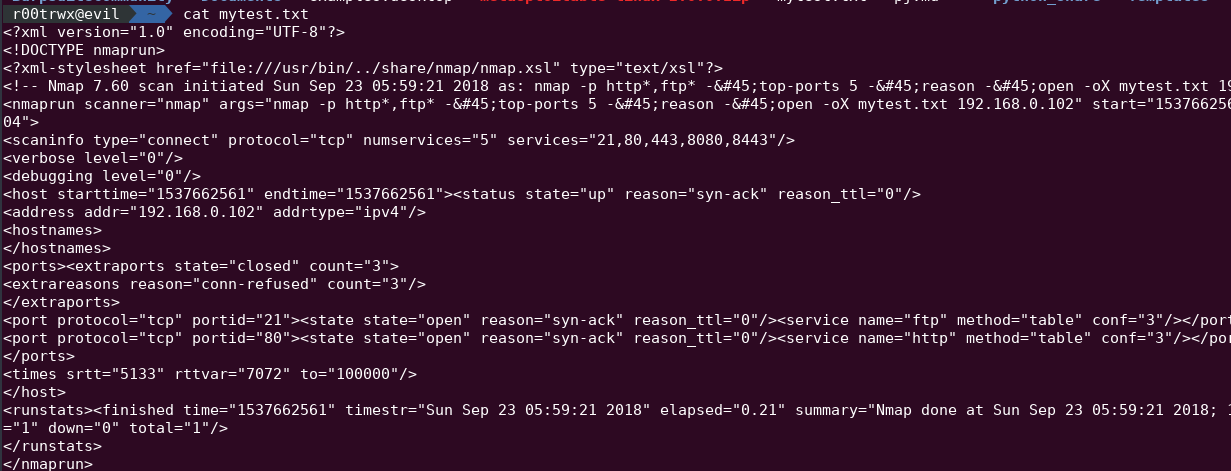
Port Scanning
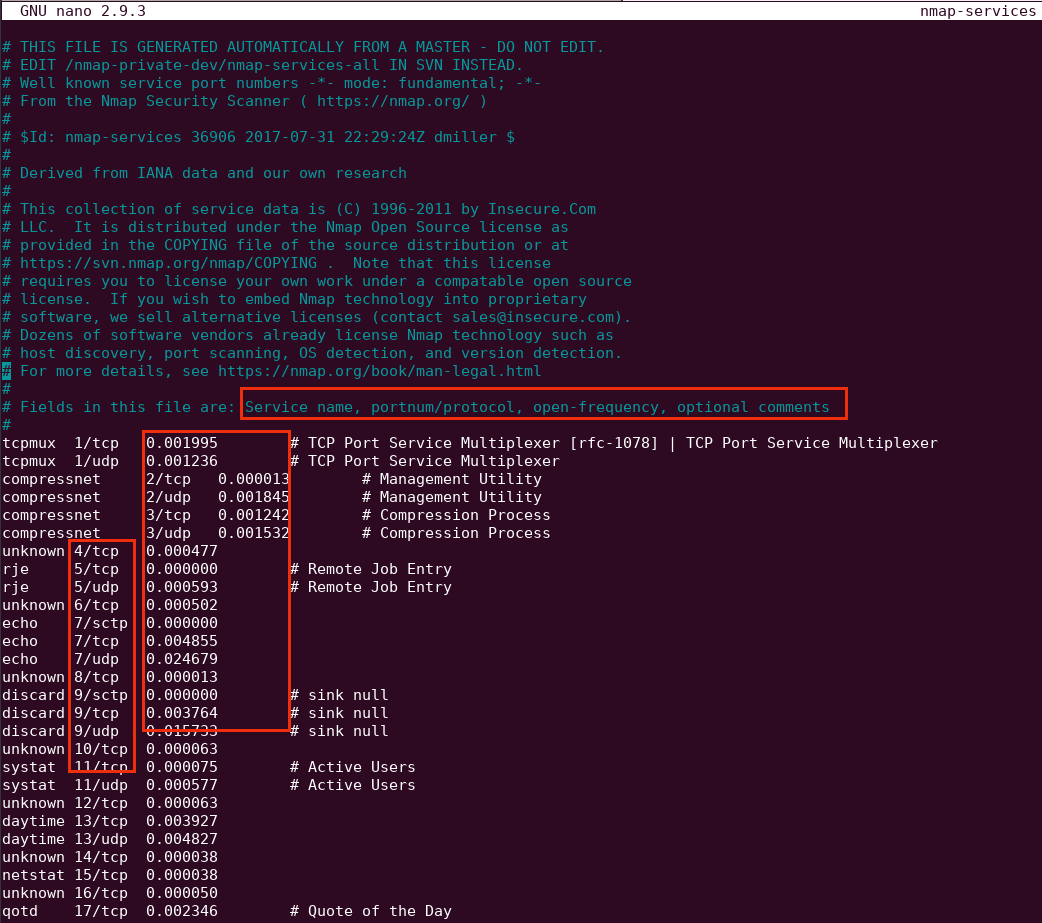
Before talking about port scanning, lets know about nmap-services file present under the data files of Nmap. Nmap has total of 12 data file which includes both directories and files and nmap-services is one of it. It is a configuration file which includes database of all the ports which Nmap uses to scan on target with its Service name, port number/protocol, open-frequency,optional comments
Port Specification
It is somewhat similar to target expansion because the way we specify target IPs as value in Nmap, the same is in the port specification. Basic way to specify destination port is given below
- -p(port number):
Using -p, you can specify port no. in various ways like using list,ranges
List : 80,443,543
Range: 80-500
nmap -p 80,443,553,130-1000 192.168.0.104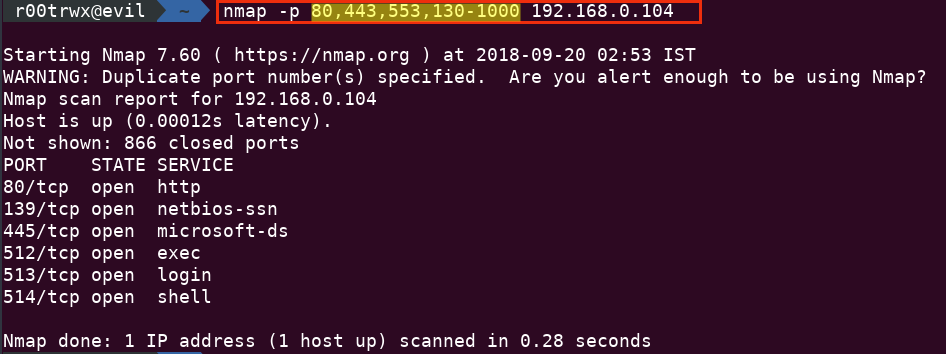
In this image I have passed both range(130-1000) and list (80,443,553)
Another example but this time I have reduced the Port Range (130-500)
nmap -p 80,443,130-500 192.168.0.104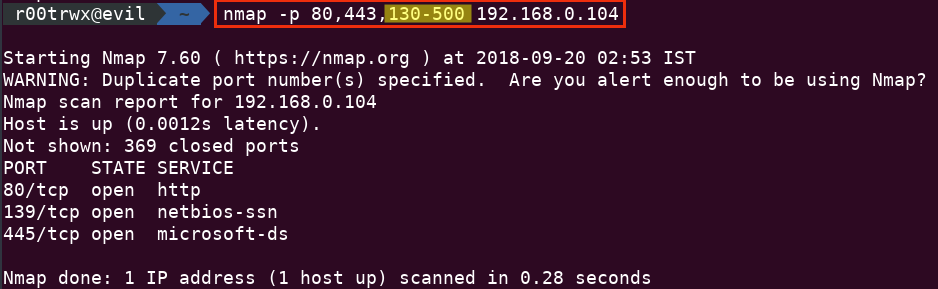
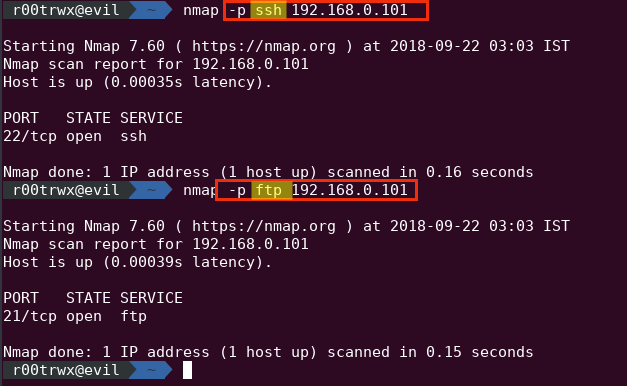
We can scan ports by passing service name using different methods like :
- Name : ssh | ftp or any service name
nmap -p ssh 192.168.0.101nmap -p ftp 192.168.0.101
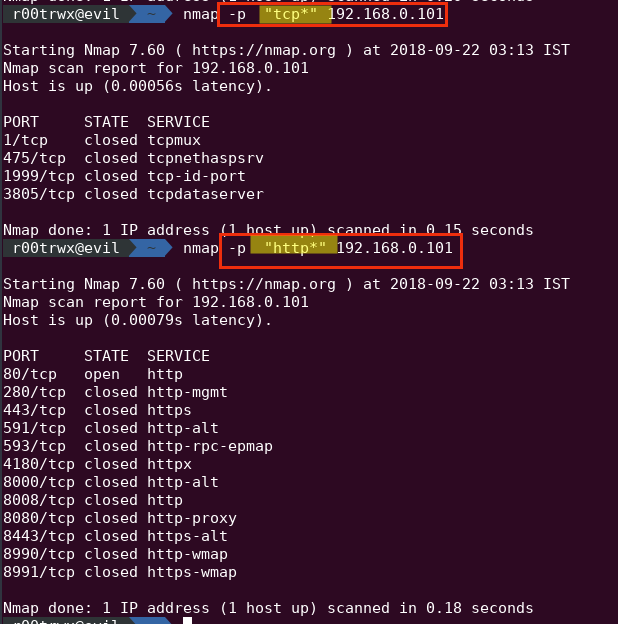
- Wildcard : "*"
By using wildcard, you can scan all the ports which will be available to your matching in nmap-services file
Example : "http*"
nmap -p "http*" 192.168.0.101
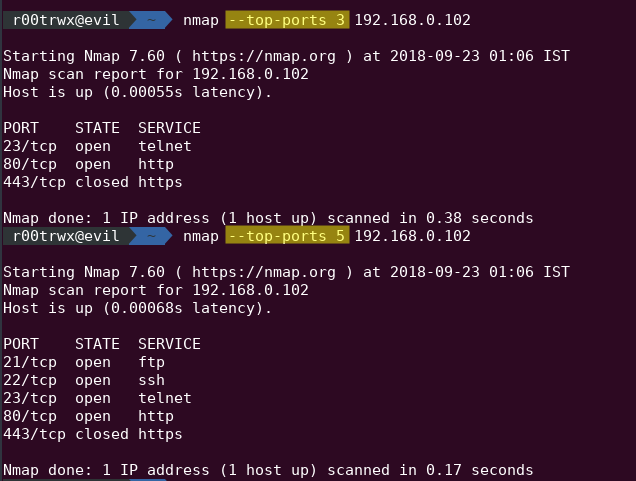
- --top-ports : We can also scan for the ports which are most likely to be opened by using the --top-ports. It looks for the frequency in nmap-services file. The service which has higher frequency will be more likely to be opened and will be on the top.
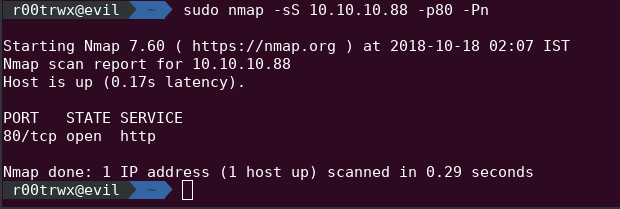
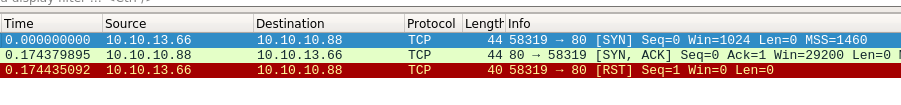
(-sS) SYN Scan
It is the first step of TCP three way handshake, In SYN scan we want to initiate connection on a port no. with the server but in the mid only we terminate it saying (Forget my request) by sending RST Flag.
In this we need raw packet privileges(means we need root access)
sudo nmap -sS 10.10.10.88 -p80 -Pn
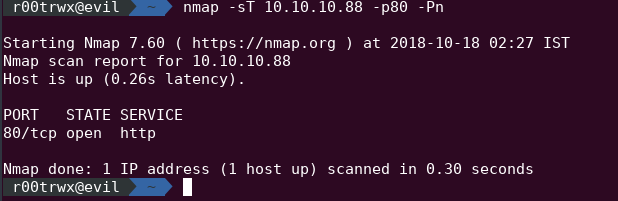
(-sT ) TCP Connect Scan
If we dont have raw packet privileges or say root access than we have another option called TCP connect scan. Nmap asks the operating system to initiate connection on target and port using system call called Connect . It is the part of programming interface which uses API calls instead of reading raw packets.
nmap -sT 10.10.10.88 -p80 -Pn
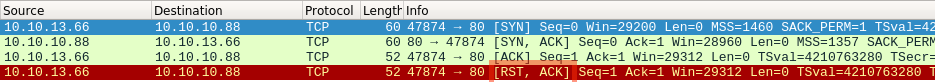
Output
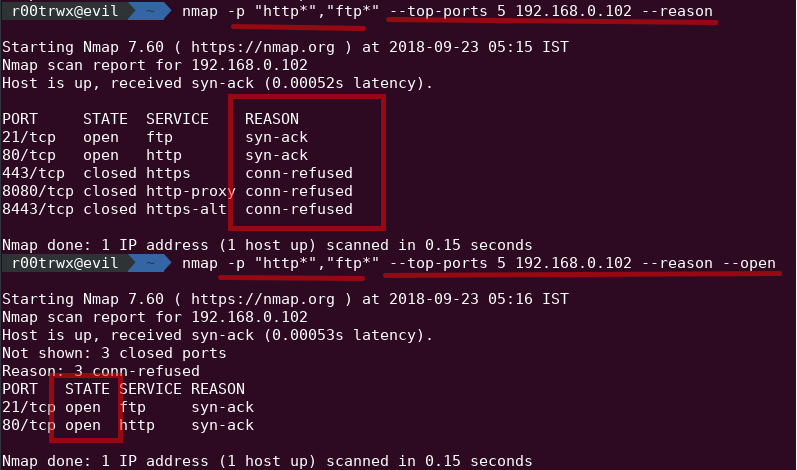
While we get our output we can again refine our results by using --reason & --open.
--reason : It will give you the reason to which discovery test, host responded to. It can be sometime confusing, as soon as Nmap gets it first response from host on a particular port it takes it as its reason.
--open : Now if you want to look for only ports which are open then you may use this --open option.
- -o:
- N,normal
- X,XML
- G,grepable
Example :
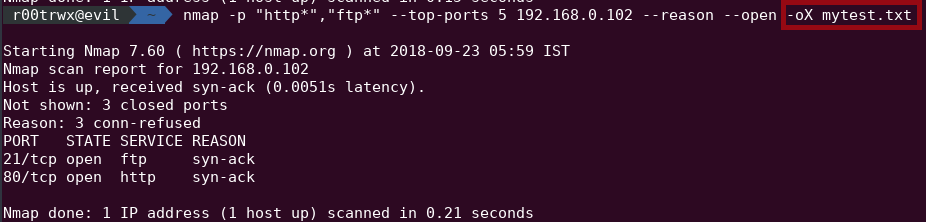
XML file :